Definition of "Wearable Computer"
Definition of what is meant by the term wearable computer,
e.g. a definition of wearable computing.
Wearable Computer Definition taken from Steve Mann's
Keynote Address
entitled "WEARABLE COMPUTING as means for PERSONAL EMPOWERMENT"
presented at the 1998 International Conference on Wearable Computing
ICWC-98, Fairfax VA, May 1998
Steve Mann
University of Toronto,
May 12, 1998
Wearable computing facilitates a new form of human--computer interaction
comprising a small
body--worn computer (e.g. user--programmable device)
that is always on and always ready and accessible.
In this regard, the new computational framework differs from that of
hand held devices, laptop computers and personal digital assistants (PDAs).
The ``always ready'' capability leads to a new form of synergy
between human and computer, characterized by long-term adaptation
through constancy of user--interface.
What is a wearable computer
A wearable computer is a
computer that is subsumed into the personal space of the user,
controlled by the user, and has both
operational and interactional constancy,
i.e. is always on and always accessible.
Most notably, it is a device
that is always with the user, and into which the user can always enter
commands and execute a set of such entered commands, and in which the
user can do so
while walking around or doing other activities.
The most salient aspect of computers, in general, (whether wearable or not)
is their
{\em reconfigurability} and their {\em generality}, e.g. that their function
can be made to vary widely, depending on the instructions provided for
program execution.
With the wearable computer (WearComp), this is no exception, e.g. the
wearable computer is more than just a wristwatch or regular eyeglasses:
it has the full functionality of a computer system but in addition to being
a fully featured computer, it is also inextricably intertwined with the wearer.
This is what sets the wearable computer apart from other wearable devices such
as wristwatches, regular eyeglasses, wearable radios, etc..
Unlike these other wearable devices that are not programmable
(reconfigurable), the wearable computer is as reconfigurable
as the familiar desktop or mainframe computer.
Wearable computing will now be formally defined in terms of its
three basic modes of operation and its six fundamental attributes.
Operational modes of wearable computing
There are three operational modes in this new interaction between human and
computer:
- Constancy: The computer runs continuously,
and is ``always ready'' to interact with the user. Unlike a
hand-held device, laptop computer, or PDA, it does not need to
be opened up and turned on prior to use. The signal flow
from human to computer, and computer to human,
depicted in
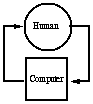 Fig 1a runs continuously to provide a constant user--interface.
Fig 1a runs continuously to provide a constant user--interface.
- Augmentation: Traditional computing paradigms are based on the
notion that computing is the primary task. Wearable computing,
however, is based on the notion that computing is NOT the primary
task. The assumption of wearable computing is that the user will be
doing something else at the same time as doing the computing.
Thus the computer should serve to augment the intellect, or
augment the senses.
The signal flow between human
and computer is depicted in
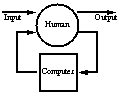 Fig 1b.
Fig 1b.
- Mediation: Unlike hand held devices, laptop computers, and PDAs,
the wearable computer can encapsulate us
(
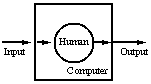 Fig 1c). It doesn't
necessarily need to completely enclose us, but the concept allows
for a greater degree of encapsulation than traditional portable
computers. There are two aspects to this encapsulation:
Fig 1c). It doesn't
necessarily need to completely enclose us, but the concept allows
for a greater degree of encapsulation than traditional portable
computers. There are two aspects to this encapsulation:
- Solitude: It can function as an information filter,
and allow us to block out material we might not wish to
experience, whether it be offensive advertising, or
simply a desire to replace existing media with different
media. In less severe manifestations, it may simply allow
us to alter
our perception of reality in a very mild sort of way.
- Privacy: Mediation allows us to block or modify information
leaving our encapsulated space. In the same way that
ordinary clothing prevents others from seeing our naked
bodies, the wearable computer may, for example, serve
as an intermediary for interacting with untrusted systems,
such as third party digital anonymous cash ``cyberwallets''.
In the same way that martial artists, especially stick
fighters, wear a long black robe that comes right down
to the ground, in order to hide the placement of their
feet from their oponent, wearable computing can also
be used to clothe our otherwise transparent movements
in cyberspace. Although other technologies, like
desktop computers, can help us protect our privacy
with programs like Pretty Good Privacy (PGP), the
achilles tendon of these systems is the space between
us and them. It is generally far easier for an
attacker to compromise the link between
us and the computer (perhaps through a so-called
trojan horse or other planted virus) than it is to
compromise the link between our computer and other
computers. Thus wearable computing can be used to
create a new level of personal privacy because it
can be made much more personal, e.g. so that it is
always worn, except perhaps during showering, and
therefore less likely to fall prey to covert attacks
upon the hardware itself. Moreover, the
close synergy between the human and computers makes
it harder to attack directly, e.g. as one might
peek over a person's shoulder while they are typing,
or hide a video camera in the ceiling above their
keyboard. Furthermore, the wearable computer can
take the form of undergarments that are encapsulated
in an outer covering or outerwear of fine conductive
fabric to protect from an attacker looking at radio
frequency emissions. The actual communications
between the wearer and other computers (and thus
other people) can be done by way of outer garments,
which contain conformal antennas, or the like, and
convey an encrypted bitstream.
Because of its ability to encapsulate us, e.g. in embodiments of
wearable computing that are actually articles of clothing in direct
contact with our flesh, it may also be able to make measurements
of various physiological quantities. Thus the signal flow
depicted in Fig 1a is also enhanced by the encapsulation
as depicted in Fig 1c.
To make this signal flow more explicit,
Fig 1c has been redrawn, in 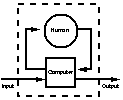 Fig 1d, where the computer and human
are depicted as two separate entities within an optional
protective shell, which may be removed or partially removed
if a mixture of augmented and mediated interaction is desired.
Fig 1d, where the computer and human
are depicted as two separate entities within an optional
protective shell, which may be removed or partially removed
if a mixture of augmented and mediated interaction is desired.
Wearable computing is a framework for enabling various degrees of each of
these three fundamental modes of operation.
Collectively, the space of possible signal flows giving rise to this
entire space of possibilities, is
depicted in
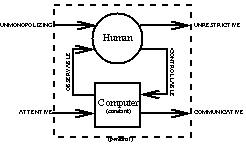 Fig 2.
Fig 2.
While individual embodiments of wearable computing may use some
mixture of these concepts, the signal path depicted in Fig 2
provides a general framework for comparison and study of these systems.
The signal paths typically each, in fact, include multiple signals, hence
multiple parallel signal paths are depicted in this figure to make
this plurality of signals explicit.
The six attributes (six signal paths) of wearable computing
There are six informational flow paths associated with this new
human--machine synergy. These signal flow paths are, in fact, attributes
of wearable computing, and are described, in what follows, from the
human's point of view:
- UNMONOPOLIZING of the user's attention:
it does not cut you off from the outside world like a
virtual reality game or the like.
You can
attend to other matters while using the apparatus.
It is built with the assumption that computing will
be a secondary activity, rather than a primary focus
of attention.
In fact, ideally, it will provide enhanced sensory
capabilities. It may, however, mediate (augment, alter,
or deliberately diminish) the sensory capabilities.
- UNRESTRICTIVE to the user: ambulatory, mobile, roving,
``you can do other things while using it'',
e.g. you can type while jogging, etc.
- OBSERVABLE by the user:
It can get your attention continuously if you want it to.
Almost--always--observable: within reasonable limitations
(e.g. that you might not see the screen while you blink
or look away momentarily) the output medium is constantly
perceptible by the wearer.
- CONTROLLABLE by the user: Responsive.
You can grab control of it at any time you wish.
Even in automated processes you can manually override to
break open the control loop and become part of the loop at
any time you want to (example: ``a big Halt button you want
as an application mindlessly opens all 50 documents that
were highlighted when you accidently pressed ``Enter''
would make a computer more CONTROLLABLE.
Infinitely--often--controllable: the constancy of
user--interface results from almost--always observability
and infinitely--often controllability in the sense that
there is always a potential for manual override which
need not be always exercised.
- ATTENTIVE to the environment:
Environmentally aware, multimodal, multisensory.
(As a result this ultimately gives the user increased
situational awareness).
- COMMUNICATIVE to others:
Can be used as a communications medium when you want it to.
Expressive: allows the wearer to be expressive through
the medium, whether as a direct communications medium to
others, or as means of assisting the production of expressive
media (artistic or otherwise).
Implied by the above six properties is that it must also be:
- CONSTANT: Always ready. May have ``sleep modes'' but
never ``dead''. Unlike a laptop computer which must be opened up,
switched on, and booted up before use, it is always on and always running.
- PERSONAL: Human and computer are inextricably intertwined.
- PROSTHETIC: You can adapt to it so that it acts as a true
extension of mind and body; after time you forget that you
are wearing it.
- ASSERTIVE:
can have barrier to prohibition or to requests by others for
removal during times when you wish such a barrier.
This is in contrast to laptop computer in briefcase or bag
that could be separated from you by a ``please leave all
bags and briefcases at the counter'' policy of a department
store, library, or similar establishment.
- PRIVATE: others can't observe or control it unless you let them.
Others can't determine system status unless you want them to,
e.g. clerk at refund counter in department store where
photography is prohibited can't tell whether or not
you are transmitting
wireless video to a spouse for remote advice,
in contrast to camcorder technology where it is obvious you
are taking a picture when you hold it up to your eye.
Note that a computer mediation device
with sufficient bandwidth can synthesize or even heighten
the augmentational aspects. For example a sufficiently ATTENTIVE
computer can sustain a sufficient illusion of being UNMONOPOLIZING
that it could encapsulate the user and still provide the same experience
as system running in the augmentational mode of operation.
Similarly, a sufficiently COMMUNICATIVE machine,
especially if ``machine'' is broadened to include mechanical mediation
devices such as motorized exoskeletons, can synthesize the UNRESTRICTIVE
attribute.
Fundamental issues of wearable computing
The most fundamental paradigm shift that
wearable computing has to offer is that of personal empowerment.
In order to fully appreciate the magnitude of this paradigm shift,
some historical examples of tools of empowerment will now be described
to place wearable computing in this historical context.
Historical context
In early civilization, individuals were all
roughly equal, militarily. Wealth was generally determined by how
many head of cattle, or how many ``mounts'' (horses) a person owned.
In hand--to--hand combat, fighting with swords, each individual
was roughly an equal. Since it was impossible to stay on a horse
while fighting, horses provided little in the way of military power,
so that even those too poor to afford to keep a horse were
not at a tremendous disadvantage to others from a fighting standpoint.
It was the invention of the stirrup, however,
that radically changed this balance. With the stirrup, it became
possible to stay on a horse while fighting. Horses and heavy
armour could only be afforded by the wealthy, and even a large group
of unruly peasants was no match for a much smaller group of mounted
cavalry. However, toward the middle ages,
more and more ordinary individuals mastered the art of fighting
on horseback, and eventually the playing field leveled out.
Then, with the invention of gunpowder, the ordinary civilian
was powerless against soldiers or bandits armed with guns.
It was not until guns became cheap enough that everyone could own one ---
as in the ``old west''. The Colt 45, for example, was known as the
``equalizer'' because it made everyone roughly equal. Even if one person
was much more skilled in its use, there would still be some risk involved
in robbing other civilians or looting someone's home.
The shift from guns to cameras and computers
In today's world, the hand gun has a lesser role to play. Wars are
fought with information, and we live in a world in which the appearance
of thugs and bandits is not ubiquitous. While there is some crime,
we spend most of our lives living in relative peace.
However, surveillance and mass media have become the new instruments
of social control. Department stores are protected with security
cameras rather than by owners keeping a shotgun under the counter
or hiring armed guards to provide a visible deterrent. While some
department stores in rough neighbourhoods may have armed guards, there
has been a paradigm shift where we see less guns and more surveillance
cameras.
The shift from draconian punishment to micro management
There has also been a paradigm shift, throughout the ages, characterized
by a move toward less severe punishments, inflicted with greater
certainty. In the middle ages, the lack of sophisticated surveillance
and communications networks meant that criminals often escaped detection or
capture, but when they were captured, punishments were extremely severe.
Gruesome corporeal punishments where criminals might be
crucified, or whipped, branded, drawn and quartered, and then burned
at the stake, were quite common in these times.
The evolution from punishment as a spectacle in which people
where tortured to death in the village square, toward incarceration
in which people were locked in a cell, and forced to attend
church sermons, prison lectures, etc., marked the first step in a
paradigm shift toward less severe punishments\cite{foucault}.
Combined with improved forensic technologies like
fingerprinting, this reduction in the severity of punishment
came together with a greater chance of getting caught.
More recently, with the advent of so--called ``boot camp'', where
delinquent youths are sent off for mandatory military--style
training, the trend continues by addressing social problems earlier
before they become large problems.
This requires greater surveillance and monitoring, but at the same
time is characterized by less severe actions taken against those who
are deemed to require these actions. Thus there is, again, still
greater chance of being affected by smaller punishments.
If we extrapolate this trend, what we arrive at is a system of social
control characterized by total surveillance and micro--punishments.
At some point, the forces applied to the subjects of the social
control are too weak to even justify the use of the word ``punishment'',
and perhaps it might be better referred to as ``micro management''.
This ``micro management'' of society may be effected by subjecting
the population to mass media, advertising, and calming music played
in department stores, elevators, and subway stations.
Surveillance is also spreading into areas that were generally private
in earlier times. The surveillance cameras that were placed in banks
have moved to department stores. They first appeared above
cash registers to deal with major crimes like holdups. But then they
moved into the aisles and spread throughout the store to deal with
petty theft. Again, more surveillance for dealing with lesser crimes.
In the U.K., cameras installed for controlling crime in rough areas of
town spread to low crime areas as well, in order to deal with
problems like youths stealing apples from street markets, or
patrons of pubs urinating on the street. The cameras have even
spread into restaurants and pubs --- not just above the cash register,
but throughout the pub, so that going out for pints, one may no longer
have privacy.
Recently, electronic plumbing technology,
originally developed for use in prisons,
for example, to prevent all inmates from flushing the toilets
simultaneously, has started to be used in public buildings.
The arguments in favor of it go beyond human hygiene and water
conservation, as proponents of the technology argue that it also reduces
vandalism. Their definition of vandalism has been broadened to
include deliberately flooding
a plumbing fixture, and deliberately leaving faucets running.
Thus, again, what we see is greater certainty
of catching or preventing people from committing lesser transgressions
of the social order.
One particularly subtle form of social control using this technology,
is the new hands free electronic showers developed for use in
prisons where inmates would otherwise break off knobs, levers, and
pushbuttons. These showers are just beginning to appear in government
buildings, stadiums, health clubs, and schools. The machine watches
the user, from behind a tiled wall,
through a small dark glass window. When the user steps toward
the shower, the water comes on, but only for a certain time, and then
it shuts off.
Obviously the user can step away from the viewing window, and then
return, to receive more water,
and thus defeat the timeout feature of the system, but this need to step away
and move back into view is enough of an irritant as to effect
a slight behavioural modification of the user.
Thus what we see is that surveillance has swept across all facets of
society, but is being used to deal with smaller and smaller problems.
From dealing with mass murderers and bank robbers, to people who
threaten the environment by taking long showers, the long arm of
surveillance has reached into even the most private of places,
where we might have once been alone. The peace and solitude of the
shower, where our greatest inspirations might come to us, has been
intruded upon with not a major punishment, but a very minor form
of social control, too small in fact to even be called a punishment.
These surveillance and social control systems are linked together,
often to central computer systems. Everything from surveillance
cameras in the bank, to electronic plumbing networks is being
equipped with fiber optic communications networks. Together with
the vast array of medical records, credit card purchases, buying
preferences, etc., we are affected in more ways, but with lesser
influence. We are no longer held at bay by mounted cavalry. More often
than being influenced by weapons, we are influenced
in very slight, almost imperceptible ways, for example, through
a deluge of junk mail, marketing, advertising, or a shower that
shuts off after it sees that we've been standing under it for too long.
While there are some (the most notable being Jeremy Bentham\cite{foucault})
who may argue that a carefully managed society
results in maximization of happiness, there are others who
argue that the homogenization of society is unhealthy, and reduces
humans to cogs in a larger piece of machinery, or at the very least,
results in a certain loss of human dignity.
Moreover, just as nature provides biodiversity, many believe that
society should also be diverse, and people should try to resist
ubiquitous centralized surveillance and control, particularly to
the extent where it homogenizes society excessively.
Some argue that micromanagement and utilitarianism,
in which a person's value may often be measured in terms of
usefulness to society, is what led to eugenics, and eventually
to the fascism of Nazi Germany. Many people also agree that,
even without any sort of social control mechanism, surveillance,
in and of itself, still violates their privacy, and is
fundamentally wrong.
As with other technologies, like the stirrup and gunpowder,
the electronic surveillance playing field is also being leveled.
The advent of the low-cost
personal computer has allowed individuals to communicate freely and easily
among themselves. No longer are the major media conglomerates the sole
voice heard in our homes. The World Wide Web has ushered in a new era of
underground news and alternative content. Thus centralized computing
facilities, the very technology that many perceived as a threat
to human individuality and freedom, has given way to low cost
personal computers that many people can afford. This is not to say that
home computers will be as big or powerful as the larger computers used
by large corporations or governments, but simply that if a large
number of people have
a moderate degree of computational resources, there is a sense of balance
in which people are roughly equal in
the same sense that two people, face to face, one with a 0.22 calibre
handgun and the other with a Colt 0.45 are roughly equal. A large
bullet hole or a small one, both provide a tangible and real risk of
death or injury.
It is perhaps modern cryptography that makes this balance even more
pronounced, for it is so many orders of magnitude easier to encrypt
a message than it is to decrypt it. Accordingly, many governments have
defined cryptography as a munition and attempted, with only limited
success, to restrict its use, and some have even defined it as a
munition.
Fundamental issues of wearable computing
The most fundamental issue in wearable computing is no doubt that of
personal empowerment, through its ability to equip the individual
with a personalized, customizable information space, owned, operated,
and controlled by the wearer. While home computers have gone a long
way to empowering the individual, they only do so when the user is
at home. As the home is perhaps the last bastion of space not
yet touched by the long arm of surveillance --- space that one
can call one's own, the home computer, while it does provide
an increase in personal empowerment, is not nearly so profound in
its effect as the wearable computer which brings this personal space ---
space one can call one's own --- out into the world.
Although wearable computing, in the most common form we know it today
(miniature video screen over one or both eyes, body worn processor,
and input devices such as
a collection of pushbutton switches or joystick held
in one hand and a microphone) was invented
in the 1970s for personal imaging
applications, it has more recently been adopted
by the military in the context of large government--funded projects.
However, as with the stirrup, gunpowder, and other similar inventions,
it is already making its way out into the mainstream consumer
electronics arena.
An important observation to make, with regards to the continued innovation,
early adopters (military, government, large multinational corporations),
and finally ubiquity, is the time scale. While it took hundreds of years
for the stirrup to be adopted by the masses, and tens of years for
guns to be adopted by the masses, the spread of computer technology must
be measured in computer years. As the technology moves faster, the military
is losing its edge. We are entering an era in which consumer electronics
is surpassing the technological sophistication of some military electronics.
Personal audio systems like the SONY Walkman are just one example of
how the ubiquity and sophistication of technology feed upon each other
to the extent that the technology begins to rival, and in some ways,
exceed, the technical sophistication of the limited--production military
counterparts such as two--way radios used in the battlefield.
Consumer technology has already brought about a certain degree of
personal empowerment,
from the portable cassette player that lets us replace the music
piped into department stores with whatever we would rather hear, to
small hand held cameras that capture police brutality and human
rights violations. However, wearable computing is just beginning to
bring about a much greater paradigm shift, which may well be equivalent
in its impact to the invention of the stirrup, or that of gunpowder.
Moreover, this leveling of the playing field may, for the first time in
history, happen almost instantaneously, should the major consumer
electronics manufacturers beat the military to raising this invention
to a level of perfection similar to that of the stirrup or modern
handguns. If this were to happen, this decreasing of the time scale
over which technology diffuses through society will have decreased to zero,
resulting in a new kind of paradigm shift
that society has not yet experienced.
Aspects of wearable computing and personal empowerment
There are several aspects and affordances of wearable computing.
These are:
- Photographic memory: Perfect recall of previously
collected information.
- Shared memory: In a collective sense, two or more
individuals may share in their collective consciousness,
so that one may have a recall of information that one
need not have experienced personally.
- Connected collective humanistic intelligence:
In a collective sense, two or more
individuals may collaborate while one or more of them
is doing another primary task.
- Personal safety: In contrast to a centralized surveillance
network built into the architecture of the city, a
personal safety system is built into the architecture (clothing)
of the individual.
- Tetherless operation: Wearable computing affords and requires mobility,
and the freedom from the need to be connected by wire to an
electrical outlet, or communications line.
- Synergy: Rather than attempting to emulate human intelligence
in the computer, as is a common goal of research in Artificial
Intelligence (AI), the goal of wearable computing is to produce
a synergistic combination of human and machine, in which the
human performs tasks that it is better at, while the computer
performs tasks that it is better at.
Over an extended period of time, the wearable computer begins
to function as a true extension of the mind and body, and no longer
feels as if it is a separate entity. In fact, the user will often
adapt to the apparatus to such a degree, that when taking it off,
its absence will feel uncomfortable, in the same way that we adapt to
shoes and clothing to such a degree that being without them
most of us would feel extremely uncomfortable whether in a public
setting, or in an environment in which we have come to be accustomed
to the protection that shoes and clothing provide.
This intimate and constant bonding is such that the combined
capabilities of the resulting synergistic whole far exceeds the
sum of either. Synergy, in which the human being and computer become
elements of each other's feedback loop, is often called Humanistic
Intelligence (HI).
- Quality of life: Wearable computing is capable of enhancing
day--to--day experiences, not just in the workplace, but in
all facets of daily life. It has the capability to enhance the
quality of life for many people.
http://wearcomp.org/wearcompdef.html
 Fig 1a runs continuously to provide a constant user--interface.
Fig 1a runs continuously to provide a constant user--interface.
 Fig 1b.
Fig 1b.
 Fig 1c). It doesn't
necessarily need to completely enclose us, but the concept allows
for a greater degree of encapsulation than traditional portable
computers. There are two aspects to this encapsulation:
Fig 1c). It doesn't
necessarily need to completely enclose us, but the concept allows
for a greater degree of encapsulation than traditional portable
computers. There are two aspects to this encapsulation:
 Fig 1d, where the computer and human
are depicted as two separate entities within an optional
protective shell, which may be removed or partially removed
if a mixture of augmented and mediated interaction is desired.
Fig 1d, where the computer and human
are depicted as two separate entities within an optional
protective shell, which may be removed or partially removed
if a mixture of augmented and mediated interaction is desired.
 Fig 2.
Fig 2.